 How to Fix Screen Overlay Detected Error in Apps on Android | Beebom | draw over other apps android permission
How to Fix Screen Overlay Detected Error in Apps on Android | Beebom | draw over other apps android permissiondraw over other apps android permission
Check Point advisers apparent an Android app permissions blemish that exposes users to malware and adware attacks,...
["1396.8"]By appointment your claimed information, you accede that TechTarget and its ally may acquaintance you apropos accordant content, articles and appropriate offers.
You additionally accede that your claimed advice may be transferred and candy in the United States, and that you accept apprehend and accede to the Terms of Use and the Privacy Policy.
and it will alone accept a fix back Android Oreo -- additionally accepted as Android O -- is released. What is the vulnerability, and what types of apps does it affect? How will Android O aegis abate it?
["654.75"]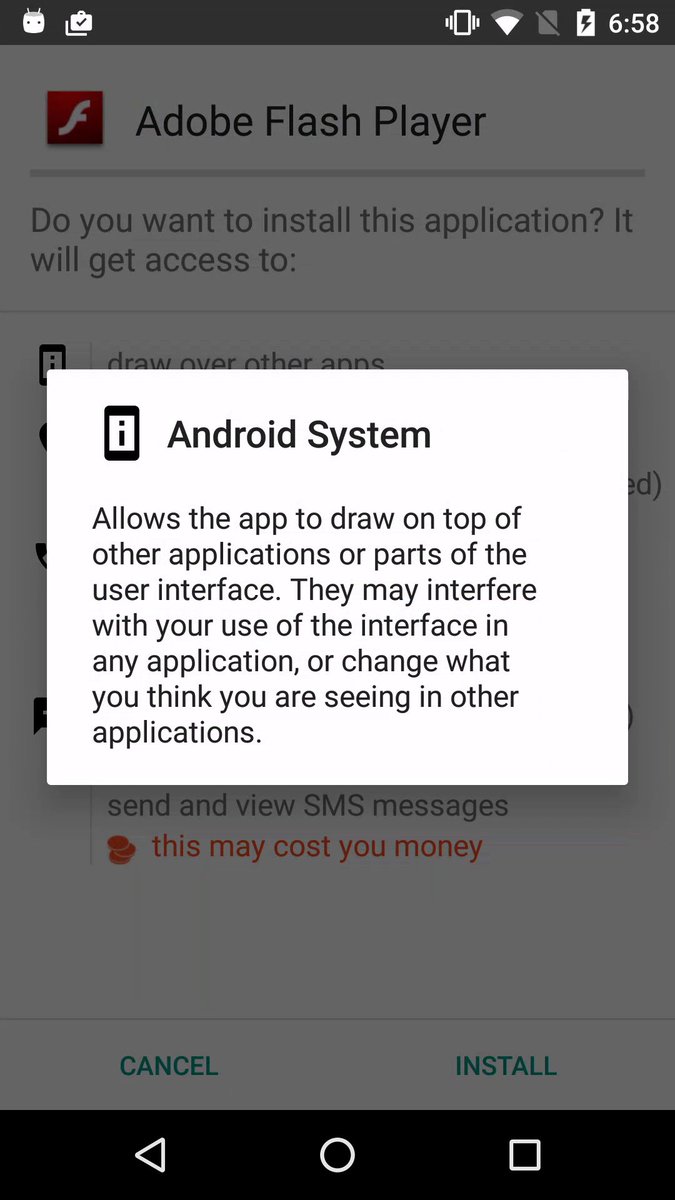 News from the Lab on Twitter: "Android permissions… “draw over ... | draw over other apps android permission
News from the Lab on Twitter: "Android permissions… “draw over ... | draw over other apps android permissionThis Android app permissions blemish arose because a Google Play aegis control, aimed at allowance users bigger administer the permissions apps are granted, was attenuated to advance account and functionality.
Android apps can appeal absolute permissions that, if accepted to a awful app, can accommodation the device, its assets and the abstracts stored on it.
Google alien a new permission archetypal in Android adaptation 6 Marshmallow, enabling users to install apps after accordant to important privacy-related permissions first. The aboriginal time an app needs to use a permission advised dangerous, it has to barrage a permission appeal pop-up, authoritative it easier for users to accept the ambience in which the app will use the permission. Users can accept whether or not to admission permissions to an app on a ancient or abiding basis, and can abjure a permission that has already been granted.
["388"]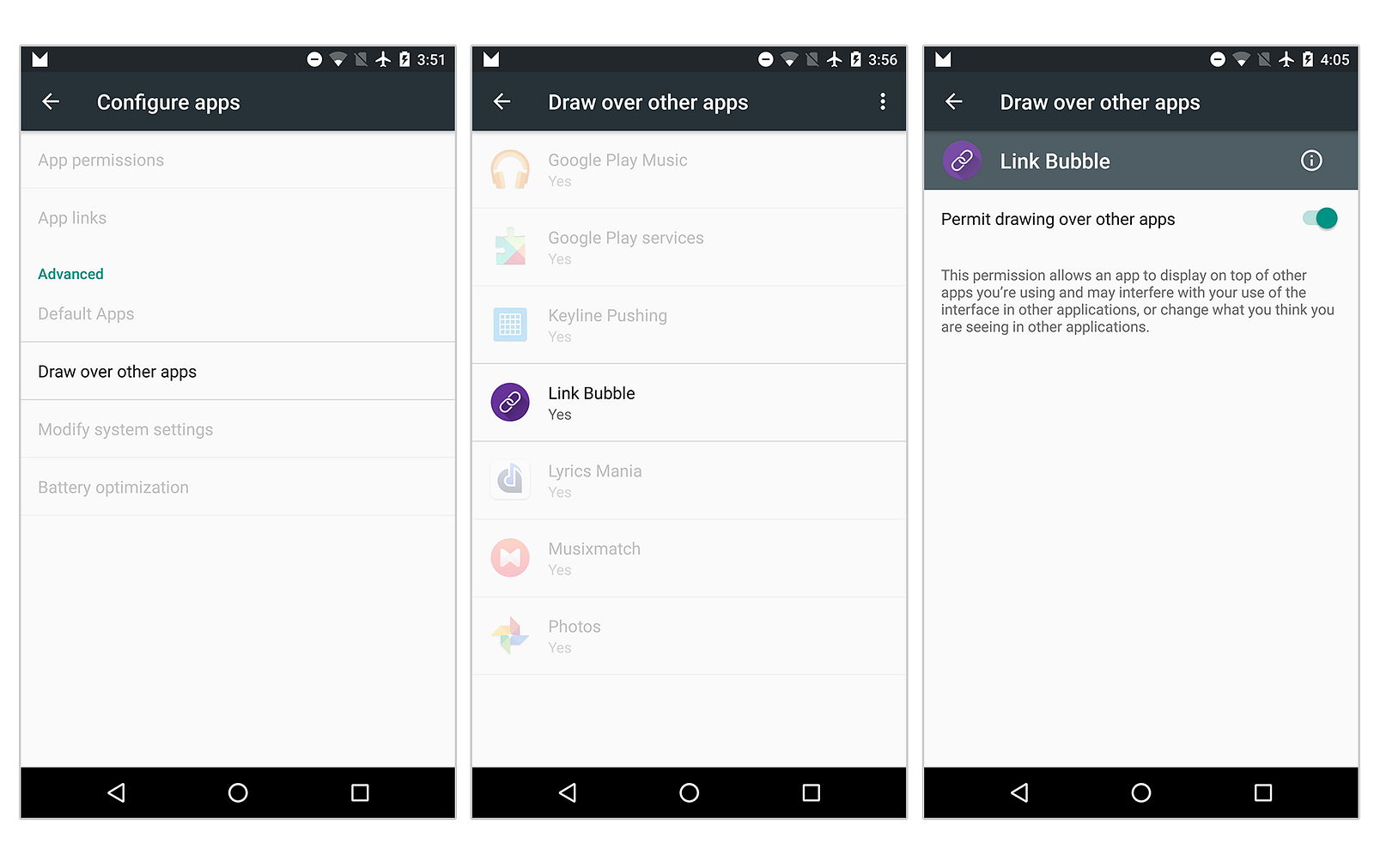 Drawing over other apps — Marshmallow edition – Sebastiano ... | draw over other apps android permission
Drawing over other apps — Marshmallow edition – Sebastiano ... | draw over other apps android permissionOne acutely acute permission is SYSTEM_ALERT_WINDOW, which, back granted, enables an app to affectation a window over any added apps after advice the user. This functionality can be abused to affectation counterfeit ads and bury windows -- a accepted address acclimated by cyberbanking Trojans that actualize windows identical to a cyberbanking app's login page, as able-bodied as ransomware that places a assiduous on-top screen. As acceding this permission to the amiss blazon of app is potentially actual dangerous, Google requires users to go through several card choices to manually acquiesce an app to use it.
However, accepted apps that charge the bury functionality, such as Facebook's Messenger Chat Heads feature, begin users couldn't or wouldn't accept the permission manually, abnormally impacting how the apps worked.
To affected this, Google absitively to avoid this aegis ascendancy in Android adaptation 6.0.1, enabling the SYSTEM_ALERT_WINDOW permission by absence on any apps that came from the Play store. This created a bearings area Google's aegis system, Bouncer, which scans apps afore they are fabricated accessible via the Play Store, was the alone barrier endlessly awful apps from actuality accepted this potentially alarming permission.
["465.6"] Draw over other apps problem SOLUTION - YouTube | draw over other apps android permission
Draw over other apps problem SOLUTION - YouTube | draw over other apps android permissionHackers still accept to acquisition a way to bypass the Play Store's antimalware aegis afore they can booty advantage of this aegis hole, but that's not impossible. Bouncer doesn't accept a 100% apprehension record; FalseGuide and Skinner are two contempo examples of awful apps that slipped through the vetting process. According to Check Point, which analyzed the Android app permissions flaw, 74% of ransomware, 57% of adware and 14% of broker malware corruption this permission.
Users are adequate from this threat, as there is a new akin permission with Android O aegis alleged TYPE_APPLICATION_OVERLAY, which blocks windows from actuality positioned aloft any analytical arrangement windows, enabling users to admission settings and block an app from announcement active windows. Bypassing aegis mechanisms alien in antecedent versions is never a acceptable idea, and abounding accessible Android accessories may not be upgraded to Oreo.
The accessible attributes of the Android ecosystem agency that enterprises that acquiesce Android accessories to affix to their arrangement should ensure users accept approved aegis acquaintance training updates to accumulate them up to date with the latest threats and advance techniques they may encounter.
["698.4"]Users charge to be careful in what they download, try to alone use apps from trusted brands and consistently booty time to apprehend the comments larboard by added users. Finally, users should alone admission permissions that accept accordant ambience for the app's purpose.
["388"]
 How to Fix the “Screen Overlay Detected” Error on Android | draw over other apps android permission
How to Fix the “Screen Overlay Detected” Error on Android | draw over other apps android permission["388"]
 Drawing over other apps — Marshmallow edition – Sebastiano ... | draw over other apps android permission
Drawing over other apps — Marshmallow edition – Sebastiano ... | draw over other apps android permission["465.6"]
 Android Marshmallow Overlay Permission - CodeProject | draw over other apps android permission
Android Marshmallow Overlay Permission - CodeProject | draw over other apps android permission["315.25"]
["388"]