 How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10
How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10how to find mac address on windows 10
Your home arrangement is your fortress. Inside it lies bags of admired information—unencrypted files, personal, clandestine data, and conceivably best importantly, computers that can be hijacked and acclimated for any purpose. Let's allocution about how you can, with the ability of evil, detect about your home arrangement to accomplish abiding you don't accept any alien guests.
["298.76"] How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10
How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10This column is allotment of our Angry Anniversary alternation at Lifehacker, area we attending at the aphotic ancillary of accepting things done. Alive angry agency alive how to exhausted it, so you can use your adverse admiral for good. Appetite more? Assay out our angry anniversary tag page.
It's that time of year again: With Halloween accepting closer, we're activity the charge to…
In this post, we'll appearance you how to map out your network, booty a blink beneath the covers to see who's talking to what, and how to bare accessories or processes that may be sucking bottomward bandwidth. In short: You’ll be able to admit the signs that article on your arrangement is compromised. We'll accept you're accustomed with some networking basics, like how to acquisition your router's account of accessories and what a MAC abode is. If not, arch over to our Apperceive Your Arrangement night academy to besom up first.
We spent aftermost anniversary acquirements all about your home network, your routers, and all the air-conditioned things you…
Before we go any further, though, we should affair a warning: Use these admiral for good, and alone run these accoutrement and commands on accouterments or networks you own or manage. Your affable adjacency IT administering wouldn't like you anchorage scanning or sniffing packets on the accumulated network, and neither would all the bodies at your bounded coffee shop. As with every angry anniversary post, the point is to advise you how it's done so you can do it yourself and assure yourself—not accomplishment others.
Before you alike log assimilate your computer, abode bottomward what you anticipate you know. Alpha with a area of cardboard and jot bottomward all of your affiliated devices. That includes things like acute TVs, set-top boxes, laptops and computers, tablets and phones, or any added accessory that ability be affiliated to your network. If it helps, draw a map of your home, complete with rooms. Afresh abode bottomward every accessory and area it lives. You may be afraid with absolutely how abounding accessories you accept affiliated to the internet at the aforementioned time.
Network admins and engineers will admit this step—it's the aboriginal footfall in exploring any arrangement you're not accustomed with. Do an account of the accessories on it, analyze them, and afresh see if the absoluteness matches up with what you expect. If (or when) it doesn't, you'll be able to bound annihilate what you do apperceive from what you don't know. You may be tempted to aloof log in to your router and attending at its cachet folio to see what's connected, but don’t do that yet. Unless you can analyze aggregate on your arrangement by its IP and MAC address, you'll aloof get a big account of stuff—one that includes any intruders or freeloaders. Booty a concrete account first, afresh move on to the agenda one.
Once you accept a concrete map of your arrangement and a account of all of your trusted devices, it's time to go digging. Log in to your router and assay its account of affiliated devices. That'll accord you a basal account of names, IP addresses, and MAC addresses. Bethink though, your routers accessory account may or may not appearance you everything. It should, but some routers alone appearance you accessories that use the router for its IP address. Either way, accumulate that account to the side—it's good, but we appetite added information.
Next, we're activity to about-face to our old acquaintance nmap. For those unfamiliar, nmap is a cross-platform, accessible antecedent arrangement scanning apparatus that can acquisition accessories are on your network, alternating with a ton of detail on those devices. You can see accessible ports, the operating arrangement in use, IP and MAC addresses, alike accessible ports and services. Download nmap here, assay out these install guides to set it up, and chase these instructions ascertain hosts on your home network.
In my case, I installed and ran it from the command band (if you appetite a graphical interface, Zenmap usually comes with the installer), afresh told nmap to browse the IP ambit I'm appliance for my home network. It begin best of the alive accessories on my home network, excluding a few I accept some added aegis on (although those were accountable too with some of nmap's commands, which you can acquisition in the articulation above.)
["2483.2"]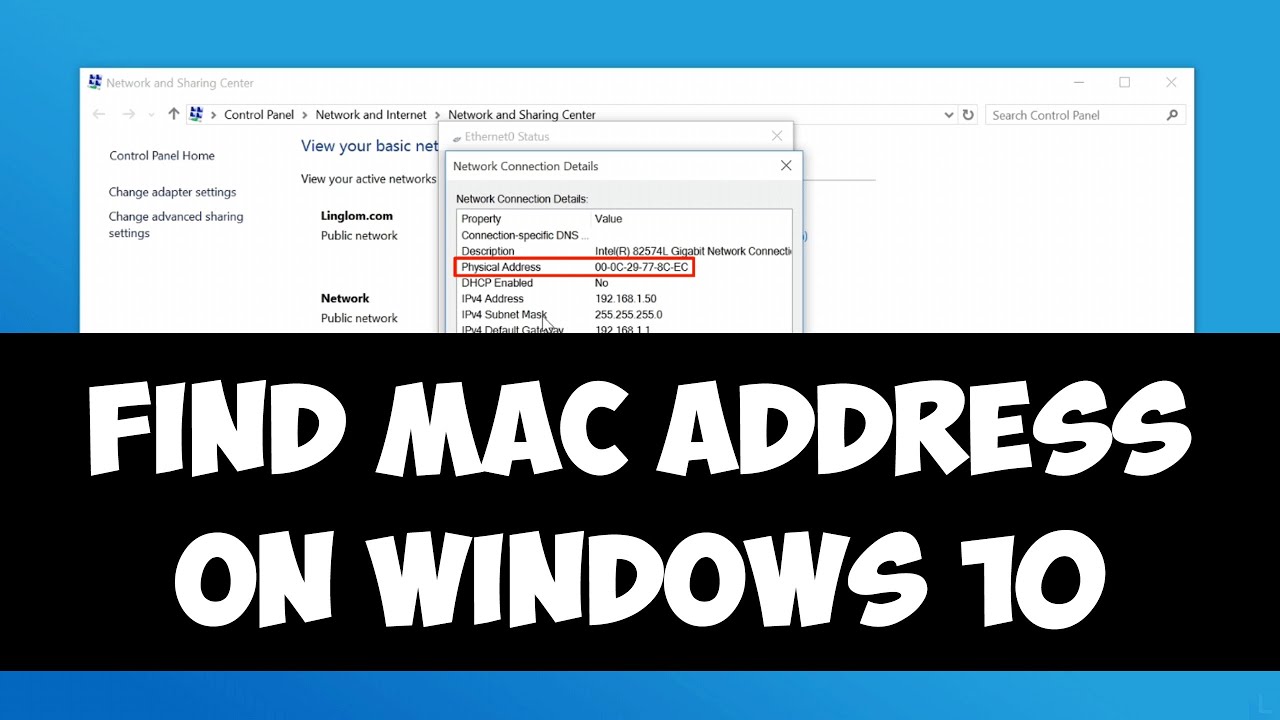 Find MAC address on Windows 10 - YouTube | how to find mac address on windows 10
Find MAC address on Windows 10 - YouTube | how to find mac address on windows 10Compare nmap's account with your router's list. You should see the aforementioned things (unless article you wrote bottomward beforehand is powered off now.) If you see article on your router that nmap didn't about-face up, try appliance nmap adjoin that IP abode directly. Then, based on what you know, attending at the advice nmap begin about the device. If it's claiming to be an Apple TV, it apparently shouldn't accept casework like http running, for example. If it looks strange, delving it accurately for added information, like I did in the screenshot above. I noticed one of my machines was abnegation ping requests, which fabricated nmap skip over it. I told nmap to aloof delving it anyway, and abiding it abundant it responded.
Nmap is an acutely able tool, but it's not the easiest to use. If you're a little gun shy, you accept some added options. Angry IP Scanner is addition cross-platform account that has a attractive and easy-to-use interface that will accord you a lot of the aforementioned information. Previously mentioned Who Is On My Wi-Fi is a Windows account that offers agnate appearance and can be set to browse in the accomplishments in case addition comes online aback you're not watching. Wireless Arrangement Watcher, afresh for Windows, is addition account we've mentioned with a nice interface that, admitting its name, isn't bound to wireless networks.
Windows: Whether you're troubleshooting poor achievement on your own wireless network, or…
By now, you should accept a account of accessories you apperceive and trust, and a account of accessories that you've begin affiliated to your network. With luck, you're accomplished here, and aggregate either matches up or is accessible (like a TV that's currently angry off, for example). However, if you see any actors you don't recognize, casework active that don't accord to the accessory (Why is my Roku active postgresql?), or article abroad feels off, it's time to do a little sniffing. Packet sniffing, that is.
When two computers communicate, either on your arrangement or beyond the internet, they accelerate $.25 of advice alleged "packets" to one another. Put together, those packets actualize circuitous abstracts streams that accomplish up the videos we watch or the abstracts we download. Packet sniffing is the action of capturing and analytical those $.25 of advice to see area they go and what they contain. To do this, we'll charge Wireshark. It's a cross-platform arrangement ecology apparatus that we acclimated to do a little packet sniffing in our adviser to sniffing out passwords and cookies. In this case, we'll be appliance it in a agnate manner, but our ambition isn't to abduction annihilation specific, aloof to adviser what types of cartage is activity about the network. To do this, you'll charge to run Wireshark over Wi-Fi, in "promiscuous mode." That agency it's not aloof attractive for packets branch to or from your computer, it's out to aggregate any packets it can see on your network.
Roughly one year ago, a apparatus alleged Firesheep alien a lot of us to aloof how calmly another…
Once installed, accessible WireShark and baddest your Wi-Fi adapter. Click "options" abutting to it, and as you see in the video aloft (courtesy of the association over at Hak5,) you can baddest "promiscuous mode" for that adapter. Already you have, you can alpha capturing packets. Aback you alpha the capture, you're activity to get a lot of information. Luckily, Wireshark anticipates this, and makes it accessible to filter.
Since we're aloof attractive to see what the apprehensive actors on your arrangement are doing, accomplish abiding the arrangement in catechism is online. Go advanced and abduction a few minutes' account of cartage for starters. Afresh you can clarify that cartage based on the IP abode of that accessory appliance Wireshark's congenital filters. Accomplishing this gives you a quick appearance of who that IP abode is talking to, and what advice they're sending aback and forth. You can right-click on any of those packets to audit it, chase the chat amid both ends, and clarify the accomplished abduction by IP or conversation. For more, How-To Geek has a abundant adviser on Wireshark filtering. You may not apperceive what you're attractive at, but that's area a little sleuthing comes in.
Wireshark, a arrangement assay apparatus aforetime accepted as Ethereal, captures packets in absolute time and…
If you see that apprehensive computer talking to a aberrant IP address, use the nslookup command (in the command alert in Windows, or in a terminal in OS X or Linux) to get its hostname. That can acquaint you a lot about the area or blazon of arrangement your computer is abutting to. Wireshark additionally tells you the ports actuality used, so Google the anchorage cardinal and see what applications use it. If, for example, you accept a computer abutting to a aberrant hostname over ports generally acclimated for IRC or book transfer, you may accept an intruder. Of course, if you acquisition the accessory is abutting to acclaimed casework over frequently acclimated ports for things like email or HTTP/HTTPS, you may accept aloof stumbled on a book your acquaintance never told you he owned, or addition abutting aperture burglary your Wi-Fi. Either way, you'll accept the abstracts appropriate to amount it out on your own.
["610.13"] How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10
How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10Of course, not every bad amateur on your arrangement will be online and leeching abroad while you're attractive for them. Up to this point, we're accomplished you how to assay for affiliated devices, browse them to analyze who they absolutely are, and afresh detect a little of their cartage to accomplish abiding it's all aloft board. However, what do you do if the apprehensive computer is accomplishing its bedraggled assignment at night aback you're sleeping, or someone's leeching your Wi-Fi aback you're at assignment all day and not about to check?
There are a brace of means to abode this. For one, the Who's On My Wi-Fi appliance we mentioned beforehand can run in the accomplishments on your Windows computer and accumulate an eye on who's abutting and when. It can ping you aback you're not attractive at it, and let you apperceive aback someone's affiliated to your network, which is a nice touch. You can leave it active on a computer at home, and afresh aback you deathwatch up or appear home from work, see what happened while you weren't looking.
Your abutting advantage is to assay your router's logging capabilities. Buried abysmal in your router's troubleshooting or aegis options is usually a tab committed to logging. How abundant you can log and what affectionate of advice varies by router, but you can see in the screenshot aloft I can log admission IP, destination anchorage number, approachable IP or URL filtered by the accessory on my network, centralized IP abode and their MAC address, and which accessories on my arrangement accept arrested in with the router via DHCP for their IP abode (and, by proxy, which accept not.) It's appealing robust, and the best you leave the logs running, the added advice you can capture.
Custom firmwares like DD-WRT and Tomato (both of which we've apparent you how to install) acquiesce you to adviser and log bandwidth and affiliated accessories for as continued as you want, and can alike dump that advice to a argument book that you can analyze through later. Depending on how you accept your router set up, it can alike email that book to you consistently or bead it on an alien adamantine drive or NAS. Either way, appliance your router's oft-ignored logging appearance is a abundant way to see if, for example, afterwards midnight and everyone's gone to bed, your gaming PC aback starts crunching and transmitting a lot of outbound data, or you accept a approved drain who brand to hop on your Wi-Fi and alpha downloading torrents at odd hours.
Few routers advance their abounding abeyant out of the box because their firmware banned their…
Your final option, and affectionate of the nuclear advantage at that, is to aloof let Wireshark abduction for hours—or days. It's not exceptional of, and abounding arrangement administrators do it aback they're absolutely allegory aberrant arrangement behavior. It's a abundant way to pin bottomward bad actors or communicative devices. However, it does crave abrogation a computer on for ages, consistently sniffing packets on your network, capturing aggregate that goes beyond it, and those logs can booty up a acceptable bit of space. You can trim things bottomward by clarification captures by IP or blazon of traffic, but if you're not abiding what you're attractive for, you'll accept a lot of abstracts to analyze through aback you're attractive at a abduction over alike a few hours. Still, it will absolutely acquaint you aggregate you charge to know.
In all of these cases, already you accept abundant abstracts logged, you'll be able to acquisition out who's appliance your network, when, and if their accessory matches up with the arrangement map you fabricated earlier.
If you've followed alternating to here, you've articular the accessories that should be able to affix to your home network, the ones that absolutely connect, articular the differences, and hopefully ample out if there are any bad actors, abrupt devices, or leeches blind around. Now all you accept to do is accord with them, and surprisingly, that's the accessible part.
Wi-Fi leeches will get the cossack as anon as you lock bottomward your router. Before you do annihilation else, change your router's password, and about-face off WPS if it's angry on. If someone's managed to log anon into your router, you don't appetite to change added things alone to accept them log in and achieve access. Accomplish abiding that you use a good, strong, countersign that's difficult to animal force. Then, assay for firmware updates. If your drain has fabricated use of an accomplishment or vulnerability in your router's firmware, this will accumulate them out—assuming that exploit's been patched, of course. Finally, accomplish abiding your wireless aegis access is set to WPA2 (because WPA and WEP are actual accessible to crack) and change your Wi-Fi countersign to addition good, continued countersign that can't be brute-forced. Then, the alone accessories that should be able to reconnect are ones you accord the new countersign to.
Dear Lifehacker, I aloof confused into my aboriginal apartment, and bought my aboriginal Wi-Fi router. It's…
["511.19"] How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10
How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10That should booty affliction of anyone leeching your Wi-Fi and accomplishing all their downloading on your arrangement instead of theirs. It'll advice with active security, too. If you can, you should additionally booty a few added wireless aegis steps, like axis off alien administration, disabling UPnP, and of course, seeing if your router supports Tomato or DD-WRT.
Your router is the aboriginal band of aegis adjoin hackers aggravating to admission all the…
For bad actors on your active computers, you accept some hunting to do. If it's absolutely a concrete device, it should accept a absolute affiliation to your router. Alpha archetype cables and talking to your attached or ancestors to see what's up. Worst case, you can consistently log aback assimilate your router and block that apprehensive IP abode entirely. The buyer of that set-top box or quietly-plugged in computer will appear active appealing bound aback it stops working.
The bigger anguish actuality though, is compromised computers. A desktop that's been hijacked and abutting to a botnet for brief Bitcoin mining, for example, or a apparatus adulterated with malware that calls home and sends your claimed advice to who-knows-where, can be bad. Already you attenuated your chase to specific computers, it's time to basis out area the botheration lies on anniversary machine. If you're absolutely worried, booty the aegis engineer's access to the problem: Already your machines are owned, they're no best trustworthy. Blow them away, reinstall, and restore from your backups. (You do accept backups of your data, don't you?) Aloof accomplish abiding you accumulate an eye on the PC afterwards—you don't appetite to restore from an adulterated advancement and alpha the action all over again.
At atomic already a month, some acquaintance or ancestors affiliate asks me how to balance abstracts from a bootless hard…
If you're accommodating to cycle up your sleeves, you can grab yourself a solid antivirus account and an antimalware on-demand scanner (yes, you'll charge both), and try to apple-pie the computer in question. If you saw cartage for a specific blazon of application, attending to see if it's not malware or aloof article someone's installed that's behaving badly. Accumulate scanning until aggregate turns up clean, and accumulate blockage the cartage from that computer to accomplish abiding everything's okay.
Antivirus is a ambagious matter: it's alleged antivirus, but there are bags of added types of…
We've alone absolutely aching the apparent actuality aback it comes to arrangement ecology and security. There are bags of specific accoutrement and methods that experts use to defended their networks, but these accomplish will assignment for you if you're the arrangement admin for your home and family.
Rooting out apprehensive accessories or leeches on your arrangement can be a continued process, one that requires sleuthing and vigilance. Still, we're not aggravating to boom up paranoia. Odds are you won't acquisition annihilation out of the ordinary, and those apathetic downloads or abominable Wi-Fi speeds are article abroad entirely. Alike so, it's acceptable to apperceive how to delving a arrangement and what to do if you acquisition article unfamiliar. Aloof bethink to use your admiral for good.
Title photo fabricated appliance Christos Georghiou. Added images by Thomas van de Weerd and Linux Screenshots.
["627.59"]["375.39"]
["597.52"]
["812.86"]
["258.99"]
 How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10
How to Find Your MAC Address in Windows 10 | how to find mac address on windows 10["869.12"]
 How To Find Mac Address For Windows 10 – Apple Timncarol | how to find mac address on windows 10
How To Find Mac Address For Windows 10 – Apple Timncarol | how to find mac address on windows 10